Spring 2012 top
1. Facebook FakeFinder
Andy Kaiser, Andrew Ruggles,
Kyle Amerman,
Riley Farrell. Mentors: Kavin Sekaran
| |
Currently, we are able to determine whether or not facebook profiles are real based on content of images and posts, number of mutual friends, and the sorts of networks that the profile is involved in...
|
2. Differences between facebook and google+
Alex Sawa, Jeff Pascus, Richard Curtis. Mentor: Minqi Luo
| |
Our project seeks to research and understand the differences between facebook and google+. We will identify the strengths and weaknesses of each as well as future capabilities of both.
In addition to the social applications, we will be investigating the academic, collaborative, scientific, and research applications of both social networks.
...
|
3. Twitter: Real or Fake?
Josh Sefton,
Morgan Soladine,
Michael Kinkoph. Mentor: Hani Dawoud
| |
For our semester project, we are looking at different Twitter accounts, real and parody accounts, while using Truthy, online surveys and reading about previous research already completed. We hope to find out what is the significance behind parody accounts and why certain people follow them.
Ultimately we hope to "Identify the most influential people on Twitter and discover who try to fool others?"
...
|
4. #SocialQuake Work Space
Brett Guiden,
Tyler Roach,
George Tattersall. Mentor: David Nemer
| |
This is the project work space for the #SocialQuake Group. We are researching the role that the Twitter has with earthquake detection, response, and relief. ...
|
5. Using Smart Phones as Digital Wallets
Insung Lee
Se Whan Park,
Tim Rast,
Lindsay Thompson. Mentors: Divya Dwarakanath,
Venkata Ponnam Shravan
| |
We are focusing our project around the question: Is the digital wallet better than the wallet that we know today? We aim to answer this question by researching the topics of security issues, ease of use and possible associated costs. ...
|
6. Design of effective health related mobile applications & Impact of interactive systems (mobile phone, computer, sensors) on users' daily behavior to foster a healthier life.
Patrick Bauer,
Sunghoon Kang,
Jinhwan Jun. Mentor: Beenish Chaudry, Liang Chen.
| |
As technology advances rapidly, it increases the people interest towards the health issues. Today, tremendous number of health related mobile application exist and devices. Our research will focus on what are the roles of these apps and devices and compare the strengths and weaknesses of them. Our focused targets are Nike + and chosen health related apps. ...
|
7. HCI issues with multiplayer online games on mobile phone
Travis Germain,
Hyung Jun Byun,
Myoungkee Ahn,
John Jones. Mentor: Wishaya Piyasirisin
| |
TTo explore HCI problems or issues of multiplayer online games on mobile phone and design a new solution to solve the problems ...
|
8. User Experience with Android, iOS, and Windows Phone 7
Murphy McGraw, Cody Frye, Joseph Crook, William Sanders. Mentor: Anhe Guo
| |
We will be evaluating the different smartphone operating systems in order to gauge why people choose them and what it is people enjoy about using them...
|
9. Social Media & The Entrepreneur
John Sibo, Matthew Cheng, Dominique Black. Mentor: Shunying An
| |
Our group, made up of the latter members: John Sibo, Matthew Cheng, Dominique Black, and mentor Shunying An were assigned to research how Entrepreneurs can use Information Technology for new business development. When given this research topic, upon meetings with the group, we discussed narrowing down our research (due to Information Technology being a very broad field.). ...
|
10. Design A Better Alarm System That Will Enhance The Wake Up Experience
Michael Spahn, Nathan Hall, Marc London, Michael Buckman. Mentor: Shreyasee Chand
| |
There are many different ways that one can wake up in the morning. Most wake up to the sound of an alarm from either a clock or a cell phone. We are researching to find out other ways to wake up in the morning and what way is the most pleasurable. This may include waking up to music instead of an alarm, waking up to the smell of something such as coffe or baccon, or waking up to movement, such as the bed or pillow vibrating. ...
|
11. Future of books in education as we develop technology for better learning environments
Tylend Dawson, Elija Moon, Becky Torrey, Jongmin Lee. Mentor: Mudit Mittal.
| |
Future of books in education as we develop technology for better learning environments ...
|
12. Exploring Copy Number Variation with Data from 1000 Genome Project
Blaine Rothrock, Tony Gao, Ryan Konz. Mentor: Andrew Younge, Yicheng Feng
| |
We are interested in investigating exome-based copy number variation among different ethnicities. Copy number variation (CNV) is a form of DNA structural variation where a section of DNA one kilobase to several megabases in size exists in higher copies or lower copies in the genome than normal. They result from structural rearrangements in DNA such as duplication, deletion, inversions, and translocations. We would like to compare exon-based CNV among different ethnicities to ...
|
Spring 2011 top
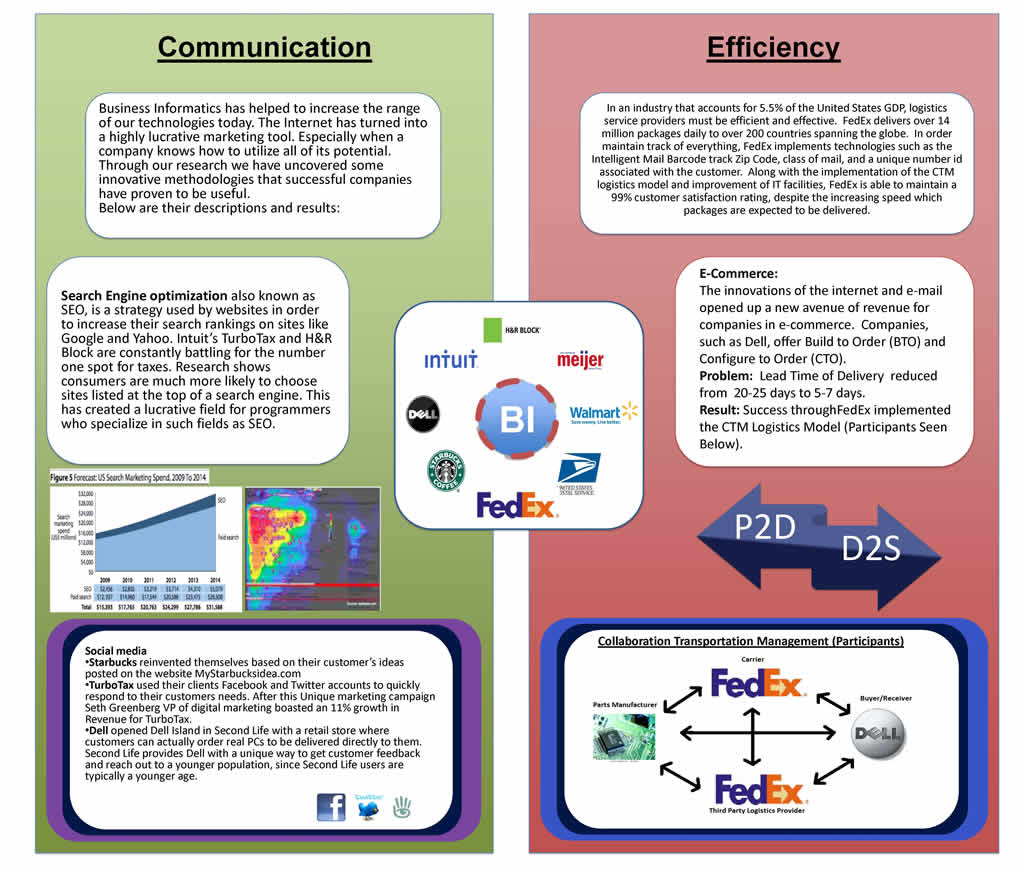
1. Business Informatics
Derik Daubenspeck, Brittney Jones, Trent Senne, Alex Stucker
|
What is the importance of Business Informatics? What technologies have positively and negatively affected business' as a result of the successful or failed implementation of them? What can be taken information/models can be taken from Business Informatics? ...
|
2. Collaboration: Enhancing Small Team Collaboration
Lucas Butler, Julian Chang, Joseph McGinn
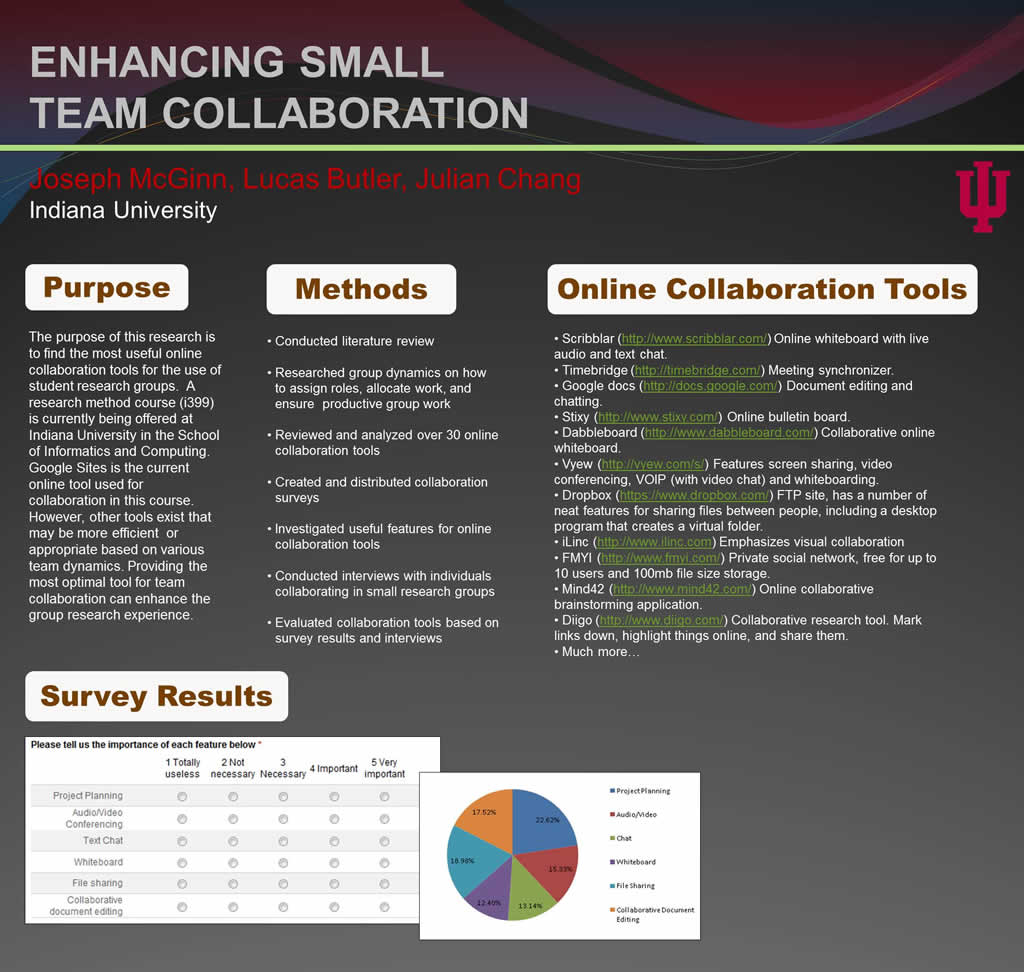 |
Our world is continuously developing more and more complex ideas and products. To be able to put together these complex ideas and products, teams and groups are needed as the end result is too complicated for just one individual to put together. Schools are becoming aware of this and are now putting an emphasis on putting students in teams to work on projects. ...
|
3. Complex Systems: Analyzing Social Patterns
Joseph Muessig, Paul Wesner, Ronnie Baldwin
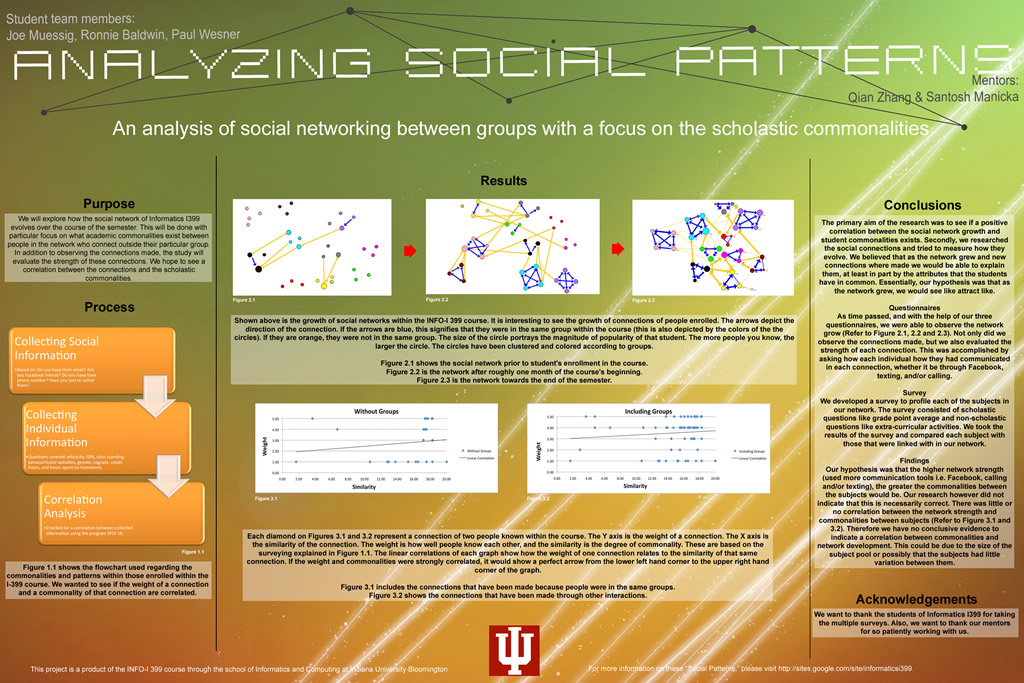 |
What are complex systems? Complex systems is a system composed of interconnected parts that as a whole exhibit one or more properties (behavior among the possible properties) not obvious from the properties of the individual parts. They can be as small or smaller than ant colonies and as large as or larger than human infrastructure. In fact, most systems utilized by human ...
|
4. Cyberinfrastructure/Bioinformatics: Analysis of Protein from the Thousand Genomes Project
Kaitlin Lisle, Kymberleigh Pagel, Alex Wu
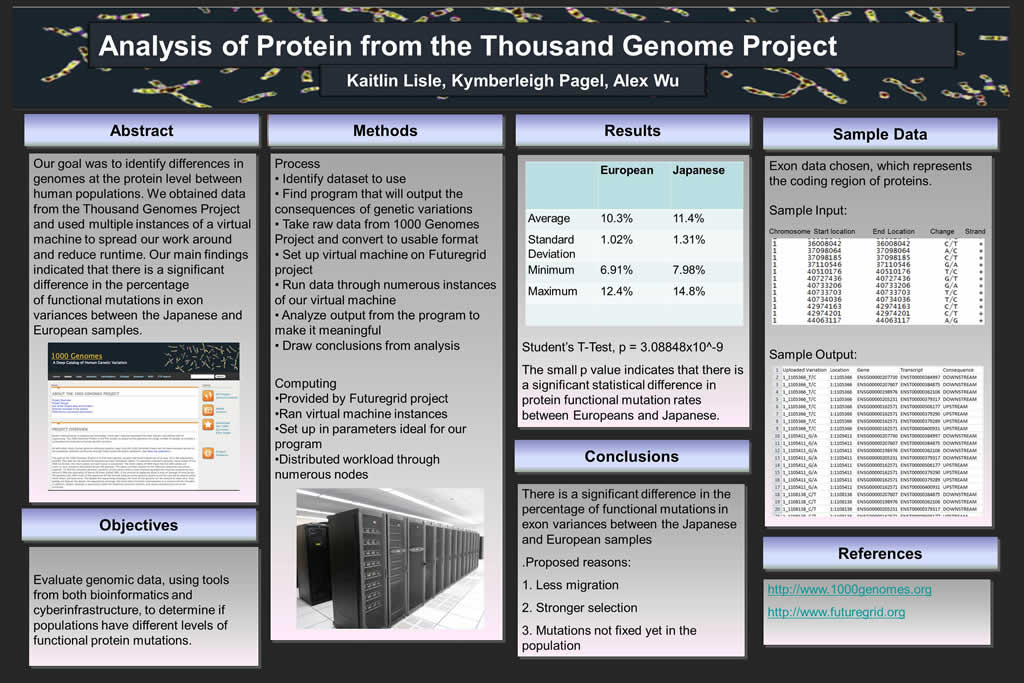 |
Each person is born with their own specific genetic variations, which is called deoxyribonucleic acid, or more commonly known as DNA. In studying these variations, scientists can determine how each variation results in a specific human trait or characteristic. However, the process of deciphering these variations has been notoriously difficult since the methods needed ...
|
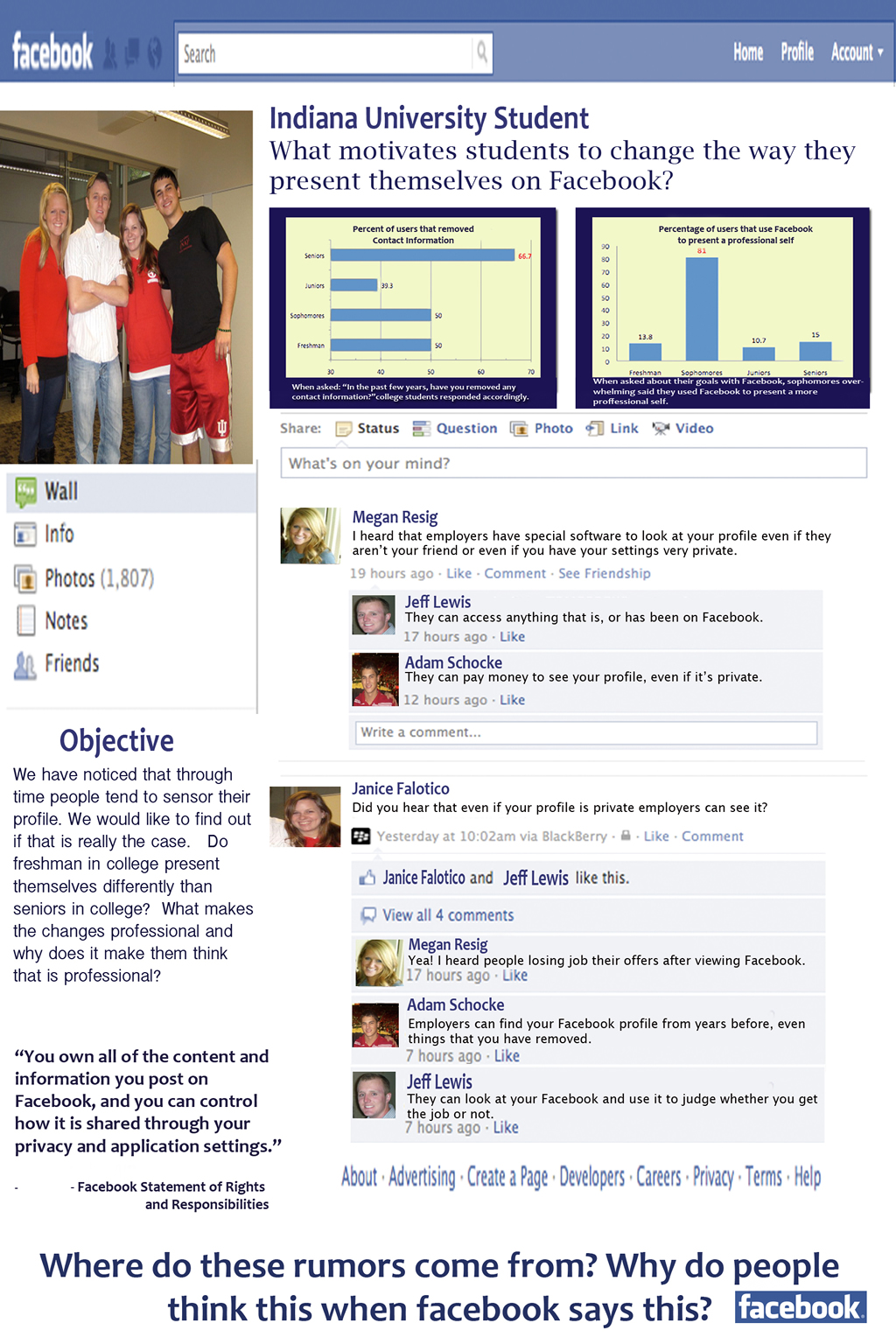
5. HCI : How Rumors Influence Us
Janice Falotico, Jeff Lewis, Megan Ressig, Adam Schocke
|
With the enormous popularity Facebook has
achieved, it comes as no surprise that
employers would start digging up what
information they could about current and
potential employees. There are an increasing
number of reports about people losing ...
|
6. Health Informatics: The New Era of Healthcare Technology
Garrett Kolb, Joshua Apkin, Youngkyu So

|
Healthcare informatics is the most pressing issue in regards to improving the quality of health care. The health sector is extremely new in regards to technology and much research is still required before a knowledgeable understanding of how it all works is obtained. Our research project's overlying goal was to further and build upon prior research that has been completed ...
|
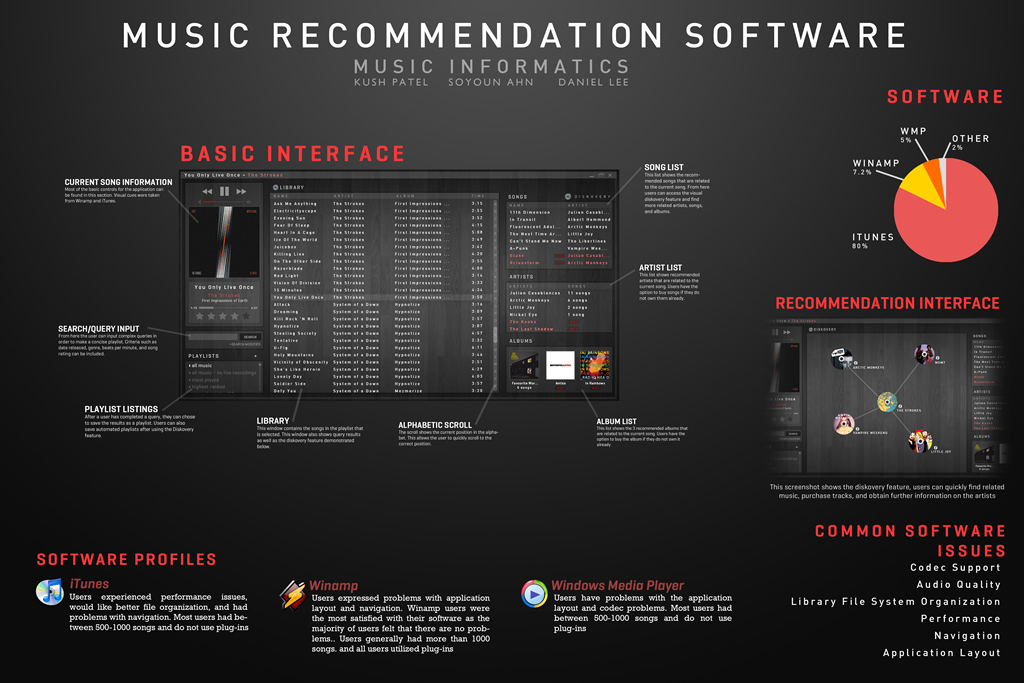
7. Music Informatics/HCI: Music Database Visualization
Daniel Lee, Kush Patel, Soyoun Ahn
|
The research goal was to identify current problems with music software and ultimately create our own prototype by implementing new and experimental database visualization methods. Our
primary research provided our group with the information to make a prototype with many great features taken ...
|
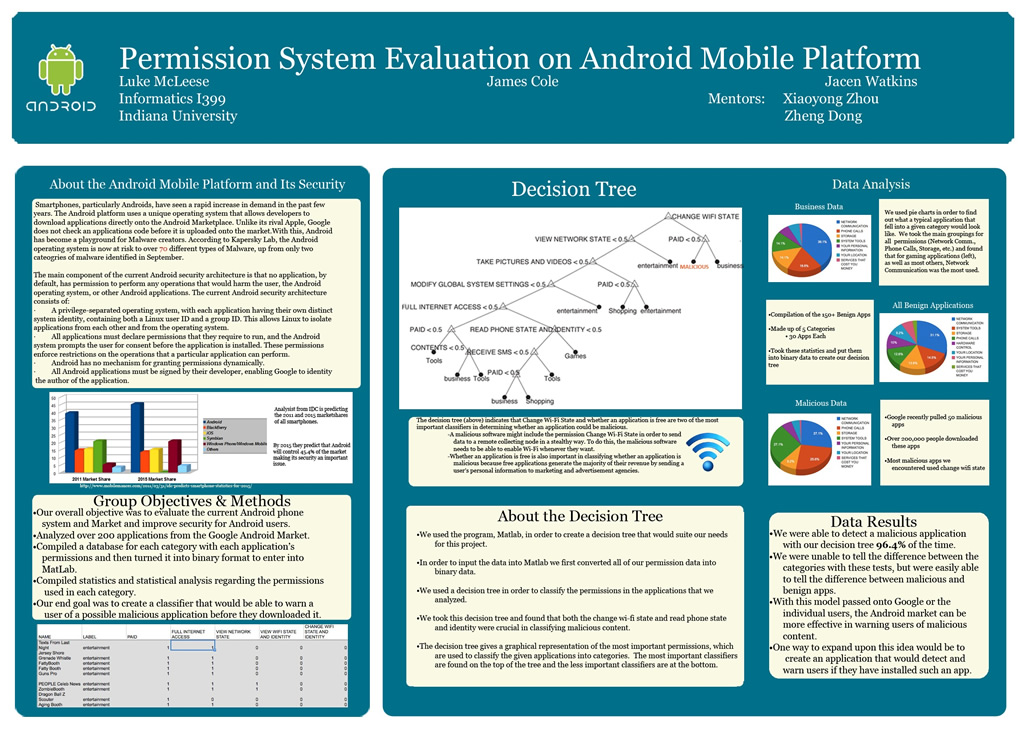
8. Security: Permission System Evaluation on the Android Mobile Platform
Luke McLeese, Jacen Watkins, James Cole
|
Over the past few years, smartphones have become increasingly ubiquitous in the daily life of people everywhere. With this, smartphone users are using their mobile devices to store and handle a significant amount of personal information on a daily basis. In order to maximize ...
|
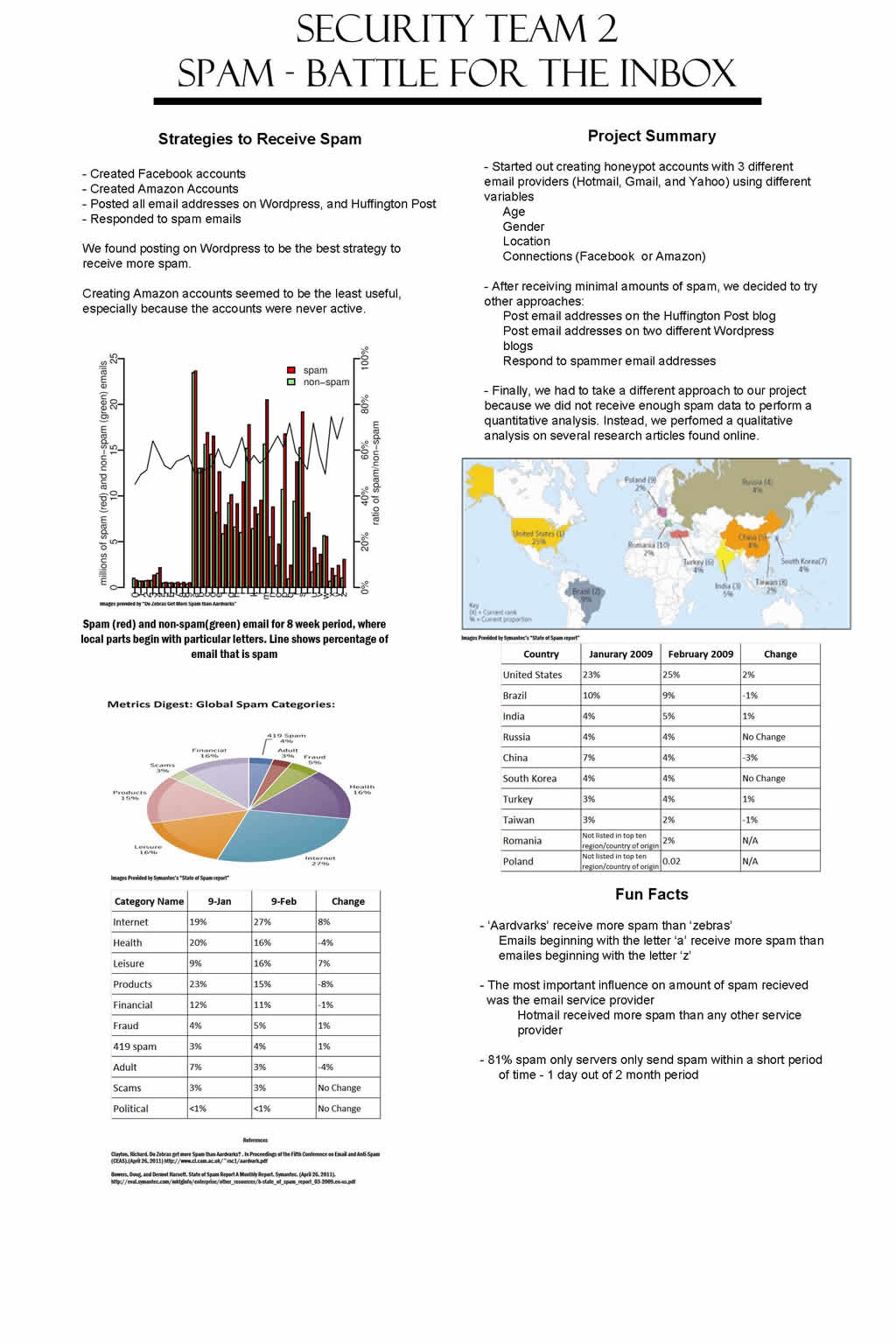
9. Security: Spam – A Battle For The Inbox
Andrew Myers, Brian Merkel, and Will Hubbard
|
Today spam can be considered a big problem in today's world. The aim of our research project is to gain some insight on the specific targeting of spam. There are many problems with spam including the economics of spam. Since the price of spam is almost all paid for by the recipients of spam, spam is a big problem for some companies ...
|
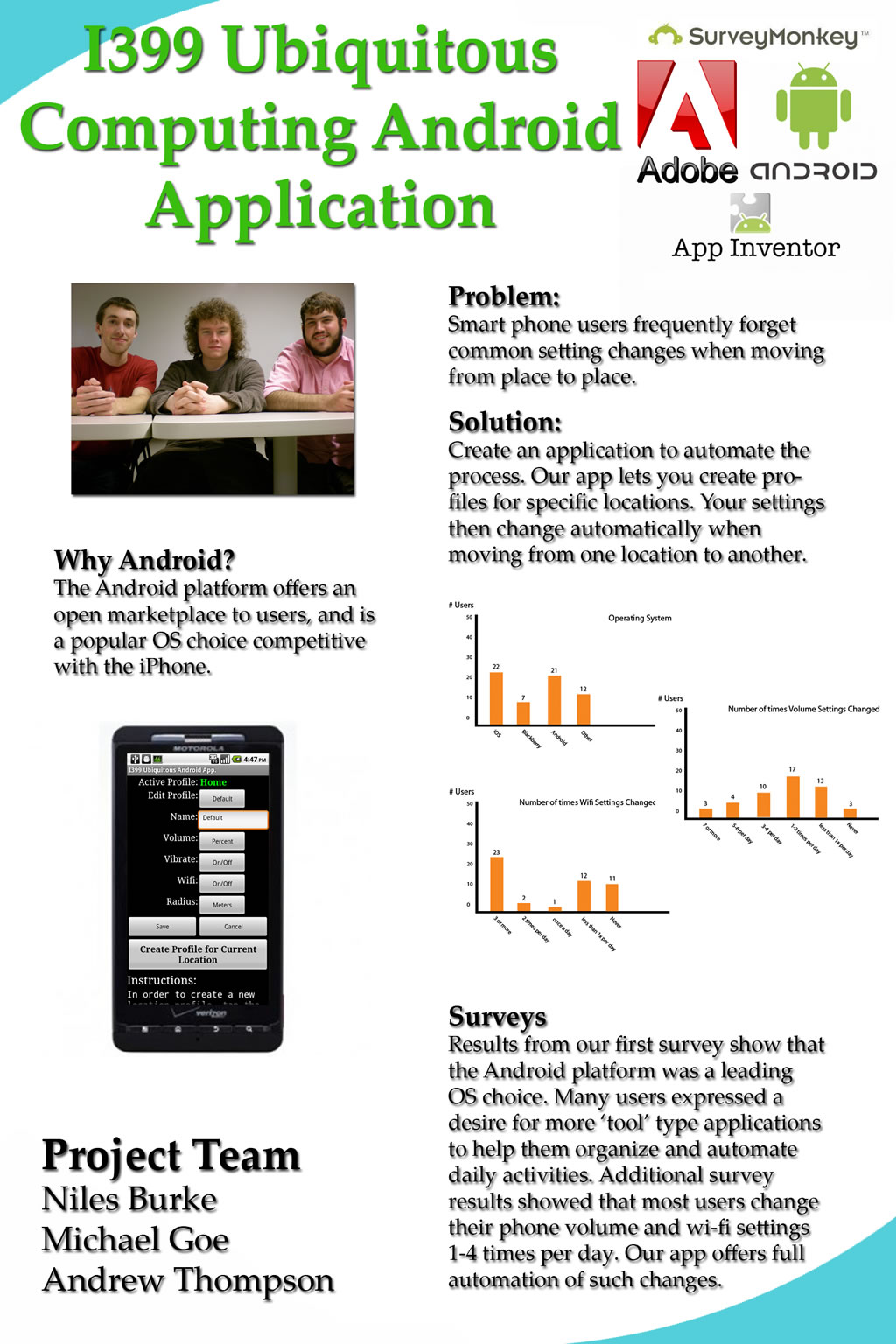
10. Ubiquitous Computing
Niles Burke, Michael Goe, Andrew Thompson
|
The Android market constitutes an open resource for fledgling application designers. As a kind of software commons it affords designers an invaluable chance to prototype and field test new software. Numerous applications are available for download which are designed to ease basic functionality for the average user. ...
|
Spring 2010 top
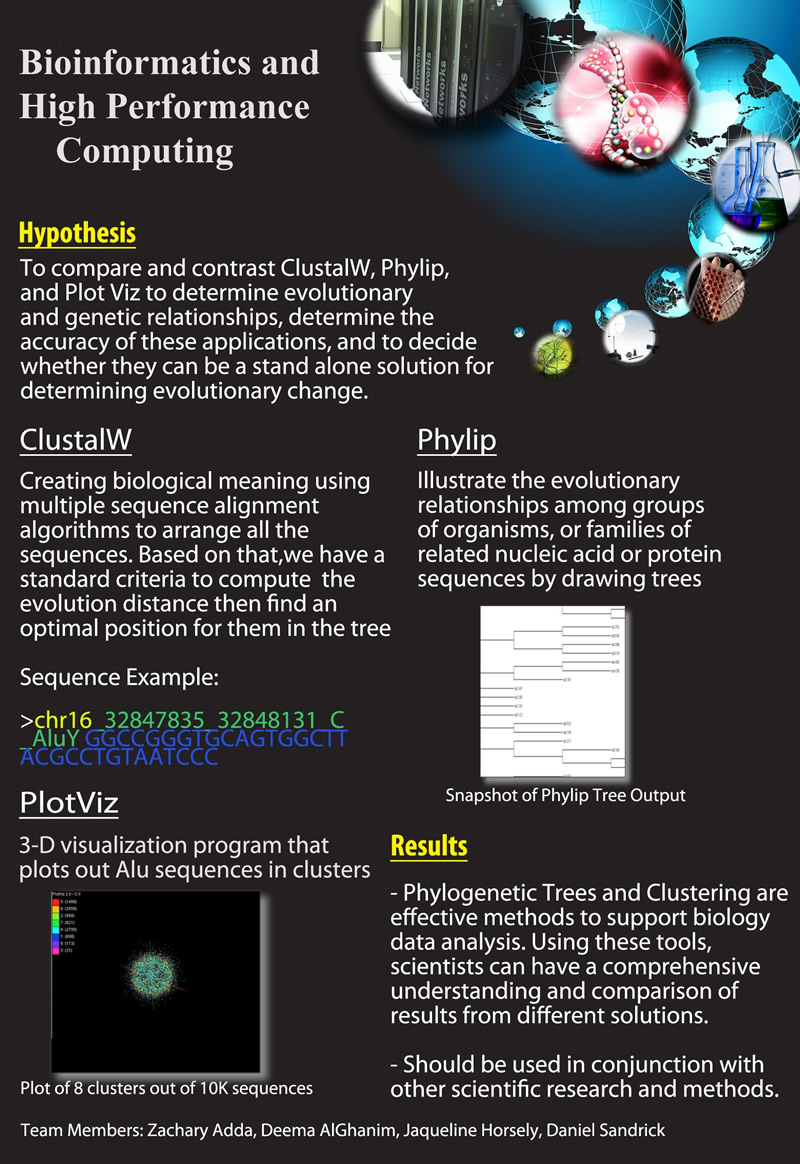
1. Bioinformatics: Bioinformatics and Supercomputing
Deema AlGhanim, Zachary Adda, Daniel Sandrick, Jaquieline Horsly
|
After doing a research in the field of Cyberinfrastructure and Bioinformatics, we have learned a lot about the field itself. But we learned even more about research, group work, and working with mentors. We have realized the importance of research for undergraduate students whether they are freshmen or seniors, and whether they ...
|
2. Data Mining: Do Integer Ratings Hinder Recommendation Systems?
Jimmy Bobowski, Amanda Lambert, Shi Hui Lim
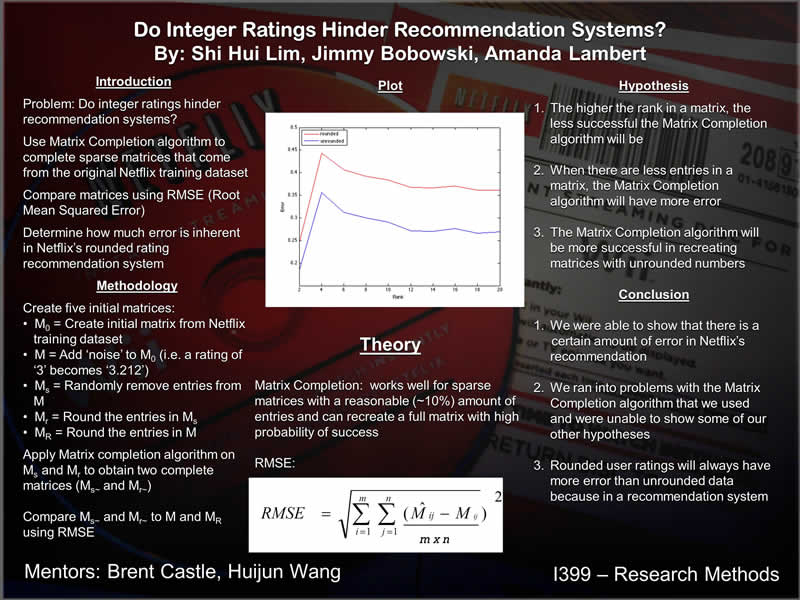 |
Use Matrix Completion algorithm to complete sparse matrices that come from the original Netflix training dataset
Compare matrices using RMSE (Root Mean Squared Error)
...
|
3. Google Wave: Usability of�Google Wave
Kody Cummins, Adam Heleine, Jenn Hughes, Mike Roche
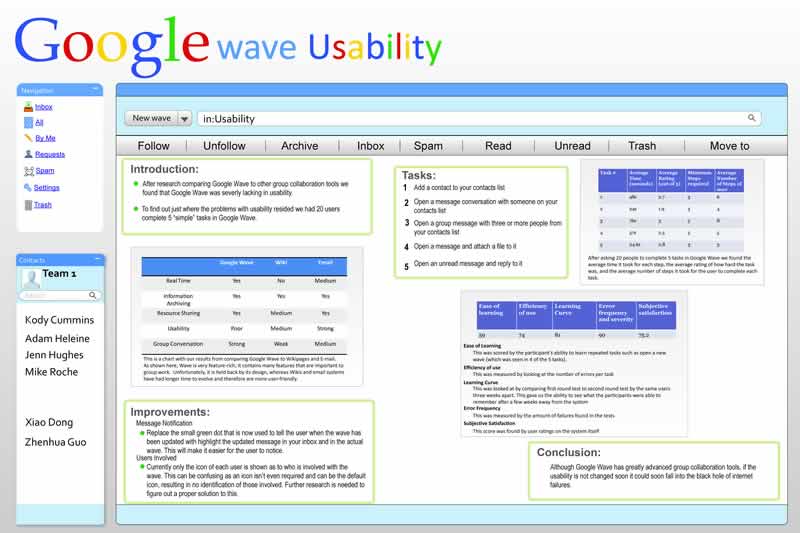 |
The value of our research to the school is that we have outlined the features and effectiveness of Wave in our project and its ability to be used for research collaboration among individuals. We have demonstrated the capabilities that Wave comes with, as well as its shortcomings; also we have shown what some people think of its usability through user testing ...
|
4. Google Wave: Exploring Google wave for Research Collaboration
Erik Kiser, Nicholas Swan, Michael Keel
 |
Google Wave is a collaborative tool developed by Google in order to solve the problem of electronic collaboration.��Our research was to specifically focus on the use of Google Wave in a collaborative ...
|
5. HCID : The Fine Line Of Acceptable Behavior - Face to Face vs. Mediated Interaction
Joseph Miller, Michael Osborn, Jaclyn Duket, Ohn'Jay Walker
|
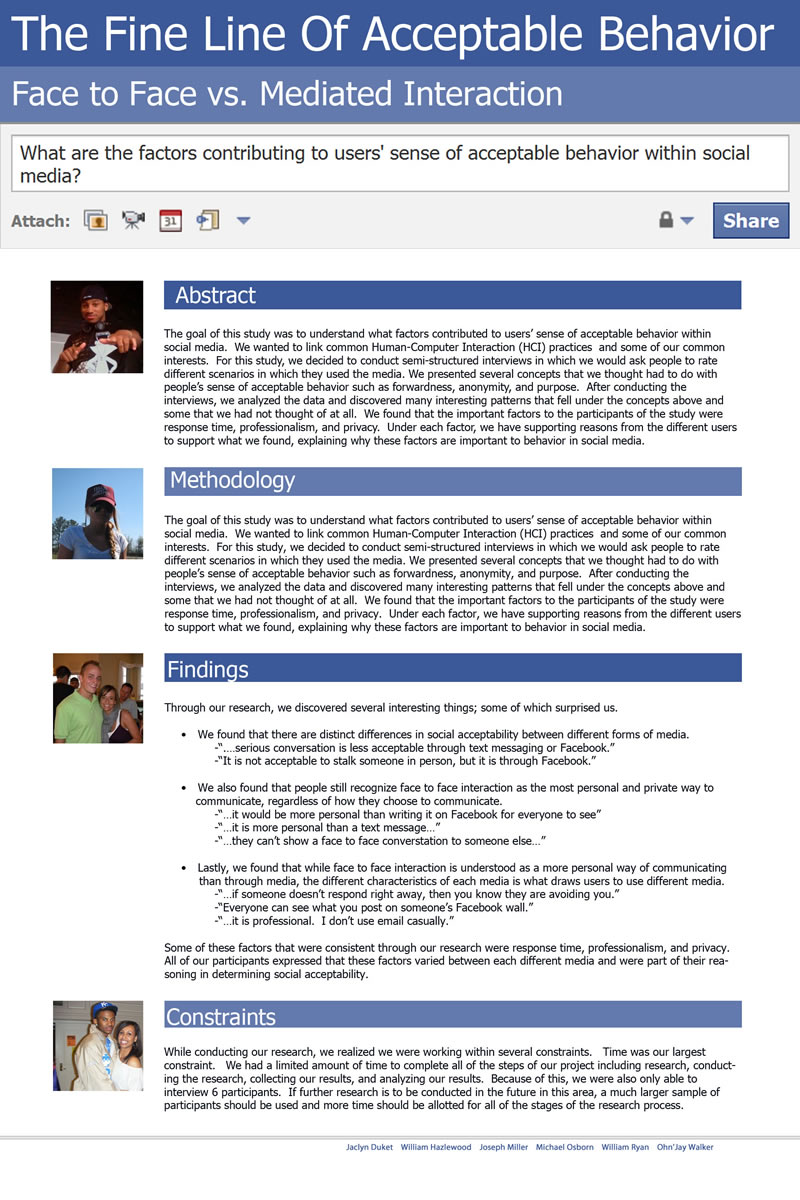
The goal of this study was to understand what factors contributed to users' sense of acceptable behavior within
social media. We wanted to link common Human-Computer Interaction (HCI) practices and some of our common
interests. For this study, we decided to conduct semi-structured interviews in which we would ask people to rate
...
|
6. Health Informatics: Health Recommender System
Alex Rogers, Austin Buono, Kate Hawkins, Tom Hortemiller
|
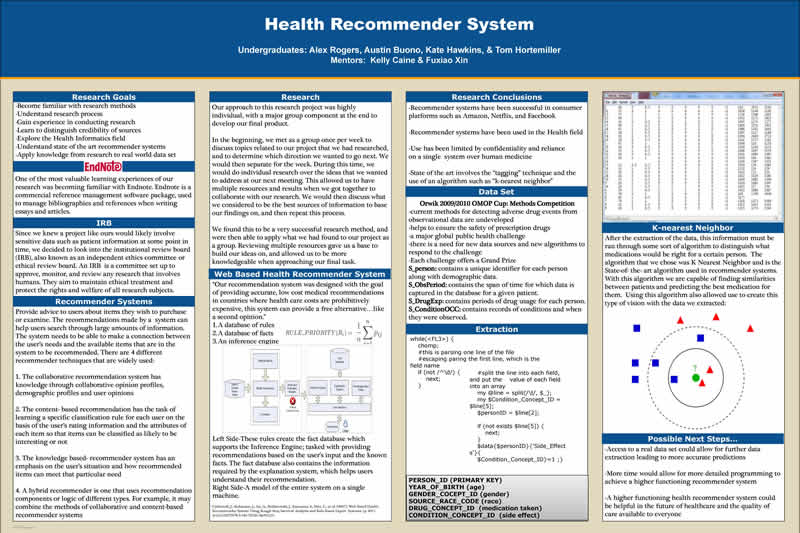
Our approach to this research project was highly individual, with a major group component at the end to develop our final product.
In the beginning, we met as a group once per week to discuss topics related to our project that we had researched, and to determine which ...
|
7. Mobile/Ubiquitous Computing
Adrian Juarez, Brad Becker, Peyman Hosseinzadeh, John Cabrera
|
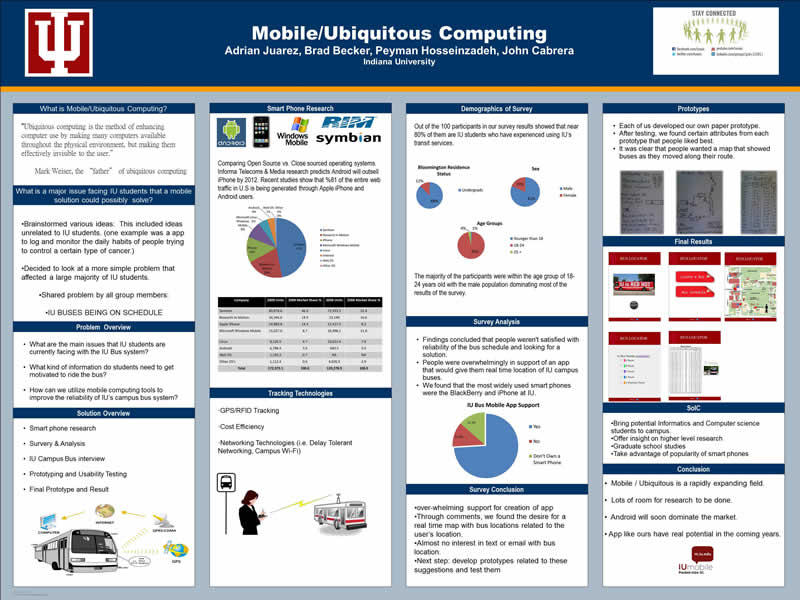
"Ubiquitous computing is the method of enhancing computer use by making many computers available throughout the physical environment, but making them effectively invisible to the user."
Mark Weiser, the "father" of ubiquitous computing
...
|
8. Research Website: SOIC Undergraduate Research Resource
Austin Graft, Veldez Joshua, Kelsey Miller
|
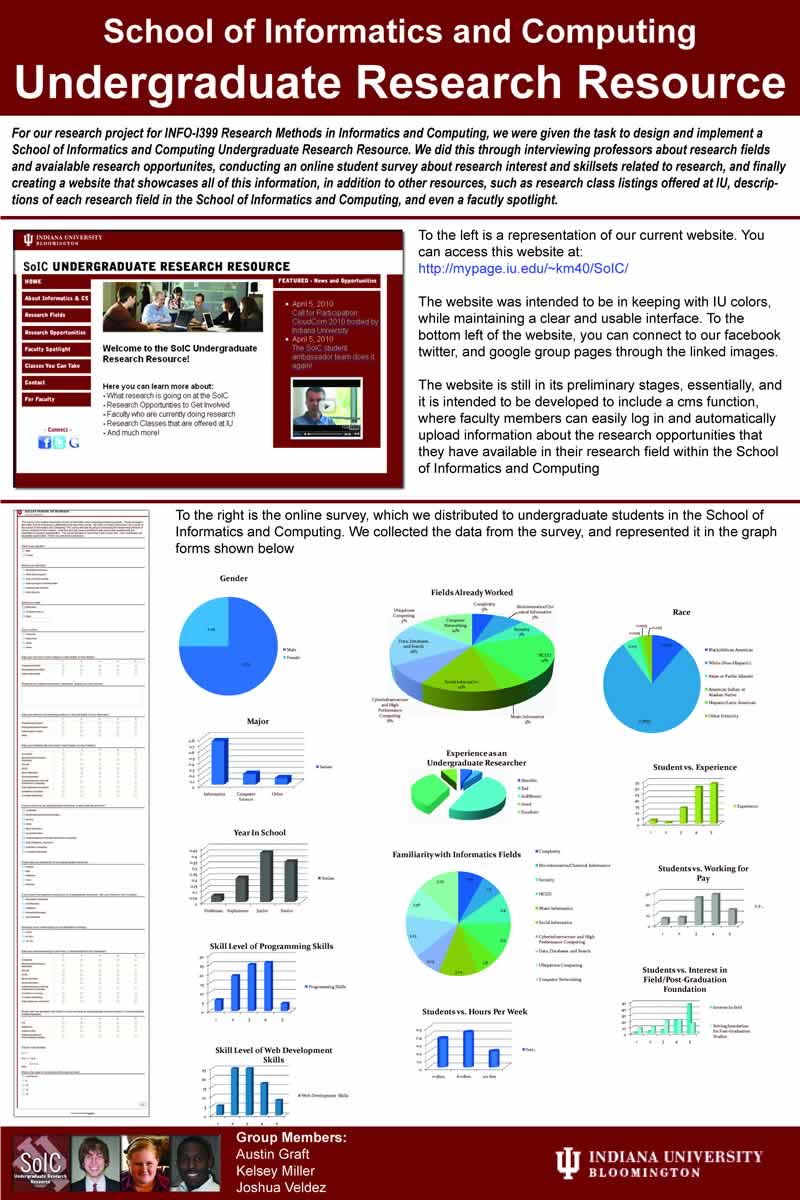
For our research project for INFO-I399 Research Methods in Informatics and Computing, we were given the task to design and implement a
School of Informatics and Computing Undergraduate Research Resource. We did this through interviewing professors about research fields and avaialable research opportunites ...
|
9. Security: Solutions to Mobile Security for the Android Operating System
Sean MacCauley, Jesse Kinser, Darin Patrick, Carter Diebold

|
As our group worked throughout the semester on the issues of security and primarily the issue of mobile security, we gained a great insight into research and mobile technology. Quite possibly one of the most important things that we learned was the importance of understanding and preventing mobile security in the future ...
|


















